The process to introduce any 3rd party tool into the ASU ecosystem is a multi-stage process put in place to safeguard ASU student and other data.
The EdPlus/ASUOnline, Information Technology Awareness Committee (ITAC) and the Enterprise Technology Learning Experience group worked together to come up with a recommended workflow for evaluating a new product. This is the recommended process to run through before adding a new tool to ASU Canvas: Pilot Evaluation and Implementation Process
While the technical process for integrating tools into the Learning Management System (LMS) is generally straightforward, we have security and contract review procedures in place to protect students, faculty, staff and the Institution. A data breach, which puts either student data, or the entire LMS infrastructure at risk could result in tremendous damage to ASU through loss of productivity due to time spent restoring the service, large expenses associated with identity protection services for students whose data is compromised, loss of confidence in ASU’s ability to protect student and Institutional data, potential lawsuits resulting from misuse of stolen data, etc.
It is for these reasons that ASU requires an application risk assessment in the form of both a Vendor IT Risk Assessment (VITRA) review (formerly ISO) before anything can be integrated into ASU’s LMS. Any product that is to be added to the LMS will need to undergo a full VITRA through Enterprise IT Risk Assessment.
Some vendors may require a Non-Disclosure Agreement (NDA) with ASU before they share any security related information. If this is the case we recommend immediately filling in the ASU Knowledge Enterprise internal NDA Request form and emailing it to industryagreements@asu.edu - the KE Agreements folks will send the vendor our standard NDA and once both parties sign, the NDA is in place.

VITRA Review
VITRA reviews are conducted by the Enterprise Technology's IT Risk Assessments group (formerly ISO). A full description of the process is available on the ET GetProtected site > Vendor IT Risk Assessment page
VITRA Review steps:
-
Check if the tool/service is either "Active" or "In Progress" in the Canvas Learning Tools Integrations list
-
Identify a person from your department/College to be the Project Manager (PM); this individual will be the project "owner" and initiate the VITRA review and work with your department Business Operations Manager (BOM) to secure a contract between ASU and the vendor
-
When you are ready to begin the security review process for a product that is to be integrated into the Learning Management System (LMS) the LMS Support team will assign a LMS Systems Administrator to work closely with your PM on the project to answer questions, sit in on the security review, and will be your contact person for installing and testing the LTI tool in our LMS environment. To request a LMS liaison contact the ASU LMS team and request that a Canvas Sys Admin is assigned to work with you on integration
From our experience, the vendor documentation submission, and the penetration tests (which on many occasions have identified problems that must be resolved before they can pass the VITRA review), have caused the longest delays.
The IT Risk Assessment team will issue a summary report outlining the risks that were identified and issue an overall Risk Rating.
- Very Low or Low risk - we can proceed immediately
- Moderate - A department level Accountable Administrator (usually the Dean or Department Head) will need to accept the risk and the financial liability of a data breach, before the tool can be installed
- High or Very High risks. - It is recommended that the vendor mitigates these risks before we proceed. High risk tools require approval from the University CFO and ASU Risk Management, before they can be integrated.
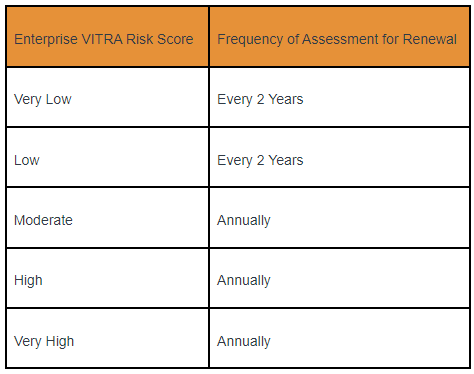
Current VITRA reviews are required by ASU Procurement before payment is issued. The renewal cycle is as follows. Learn more about the VITRA process and Risk Ratings
Testing
- During the VITRA review, we will install the tool on our DEV instance of Canvas so that you can test the tool. The DEV instance of Canvas does not have any FERPA data and can be used for testing purposes, prior to VITRA.
- The LX-Environments (Canvas Sys Admins) will install the tool in Canvas DEV and verify that it is connecting to the external service.
- It is the responsibility of the department planning to use the tool to test it and verify that it is working as promised/expected. We strongly recommend that if faculty requested the tool, you invite them to test the tool in the Canvas DEV environment.
- Contact ASU SAILS and verify that the product meet ASU and Federal ADA requirements. Please ask vendor if they have a VPAT (Voluntary Product Accessibility Template) and share this with SAILS.
-
When the tool has gone through VITRA, Contracts, etc. LX-E will install the tool in our production Canvas environment. We strongly recommend that the department team does one last round of testing in Canvas production, to make sure nothing has changed, prior to using it in a live course.
PCI Compliance
If the software includes an option for students to purchase items directly from the vendor, the project manager will need to request a PCI Compliance Review
Contract Review
A contract or purchase agreement is required between ASU and the application supplier, even if the application is being used for a no-cost pilot project. In some cases, a purchase order will be issued to the supplier, which will reference ASU’s Standard Terms and Conditions, which can be updated periodically. These terms and conditions can be found here. Alternatively, the ASU Standard Terms and Conditions may not be the proper contractual avenue based on the scope of services provided by the Supplier. In which case, Purchasing will draft an agreement that will properly address the scope of services.

Occasionally, a supplier will take exception to ASU’s Standard Terms and Conditions. Purchasing will coordinate with the supplier and department to negotiate and arrive to a final agreement. Note that there may be some exceptions to which Purchasing must seek approval from an authority other than the department; these authorities include, but are not limited to, Office of General Counsel, Risk & Emergency Management, and/or Human Resources. Purchasing will coordinate with these departments to obtain the proper approval and will reach out to the department for information, if needed.
Upon completion of the contract review, Purchasing will work with the supplier to obtain signature; Purchasing will execute the agreement on behalf of ASU and pursuant to ASU’s Contract Signature Authority policy, which can be found here.
The business manager in your department should initiate the contract review process with ASU Purchasing.
Final steps

Upon successful completion of the VITRA review (and if needed, the PCI Compliance review) the software can be integrated with the Canvas LMS system.
If the pilot does NOT need LMS integration, then the LMS team would not need to be involved and the steps related to the LMS integration process need not be undertaken, but you would still need at the minimum, a department level VITRA review to deploy the application in any form at ASU.